Matchless Tips About How To Detect Syn Attack
We’ll show you how to identify and inspect abnormal traffic.
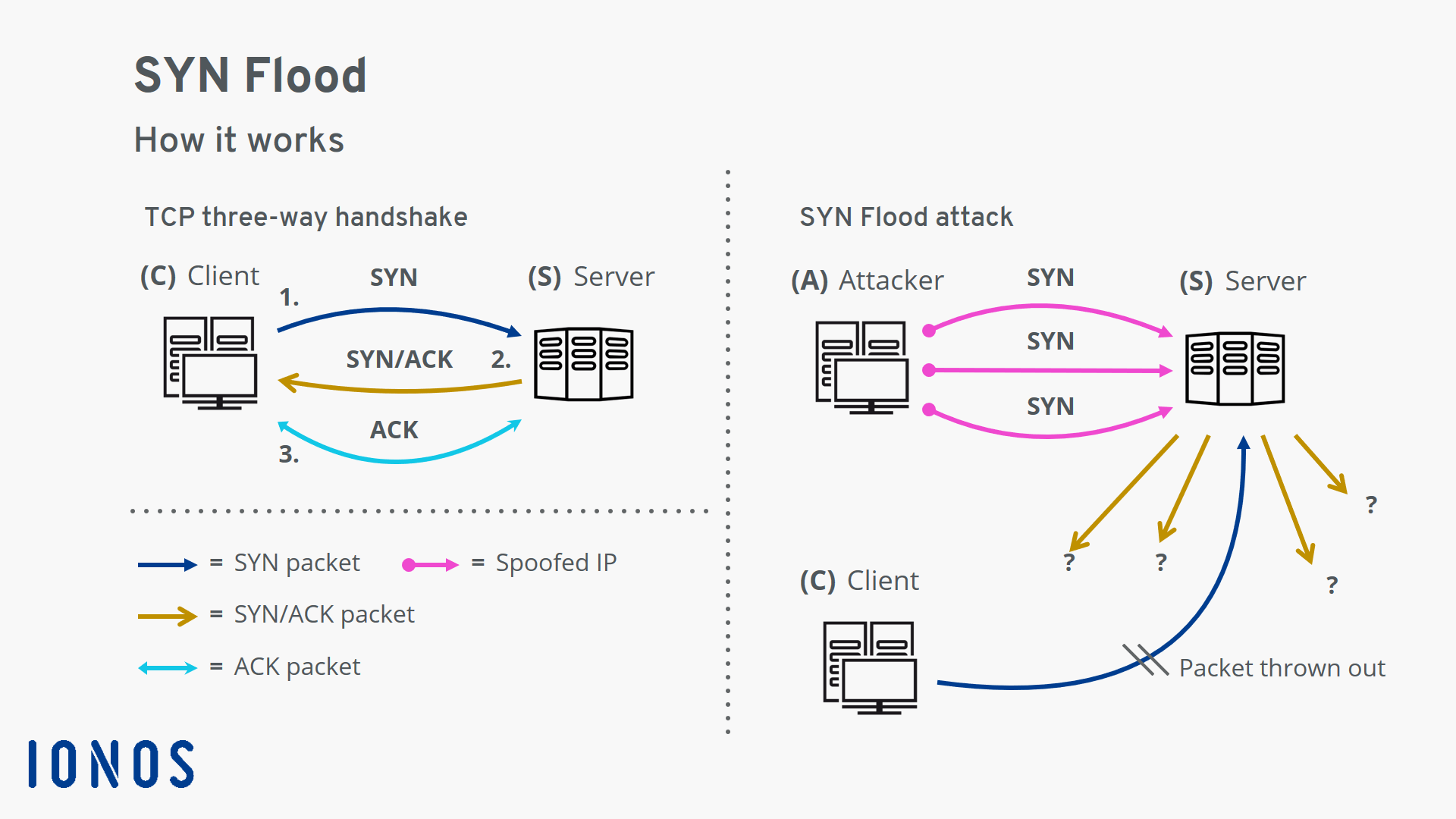
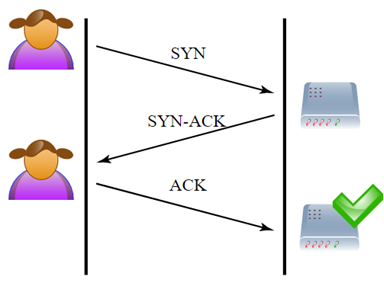
How to detect syn attack. If you are initiating the syn flood from. Then, create a rule file with the extension.rules, and add your rule to the file with all the features you need to test for the attack you want to check. 1) the customer asks for a connection by sending a syn (synchronize) message to the server.
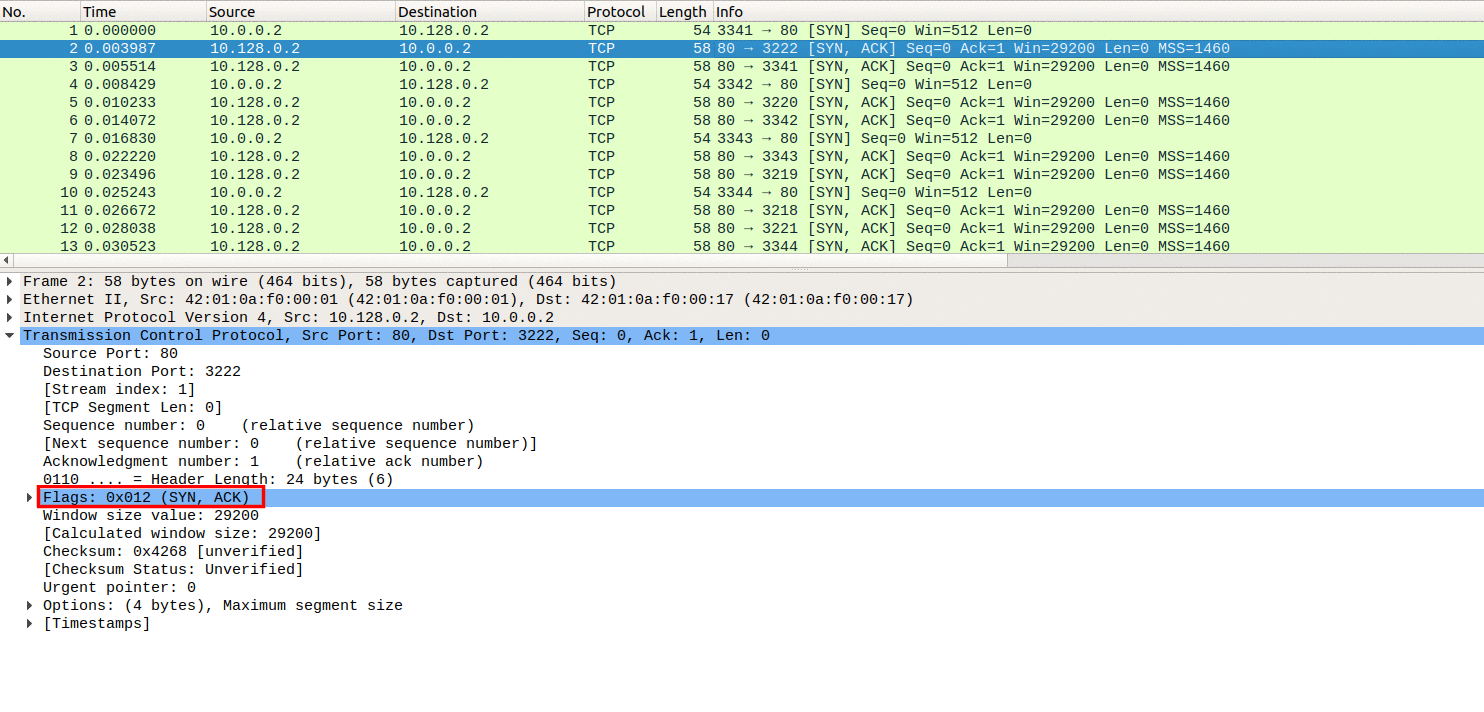
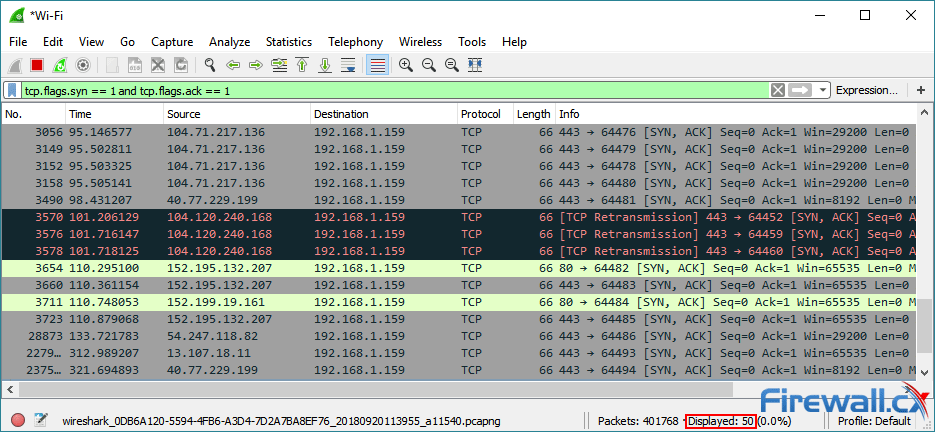
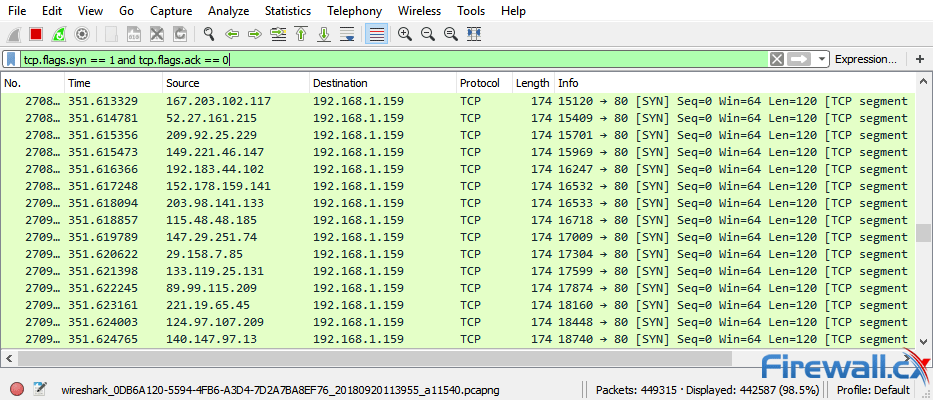
Wireshark is a strong, free solution, but paid. Tcp.flags.syn==1 and tcp.flags.ack==0 and tcp.window_size <= 1024. Here’s a wireshark filter to detect tcp syn / stealth port scans, also known as tcp half open scan:
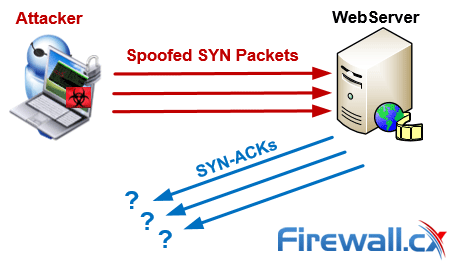
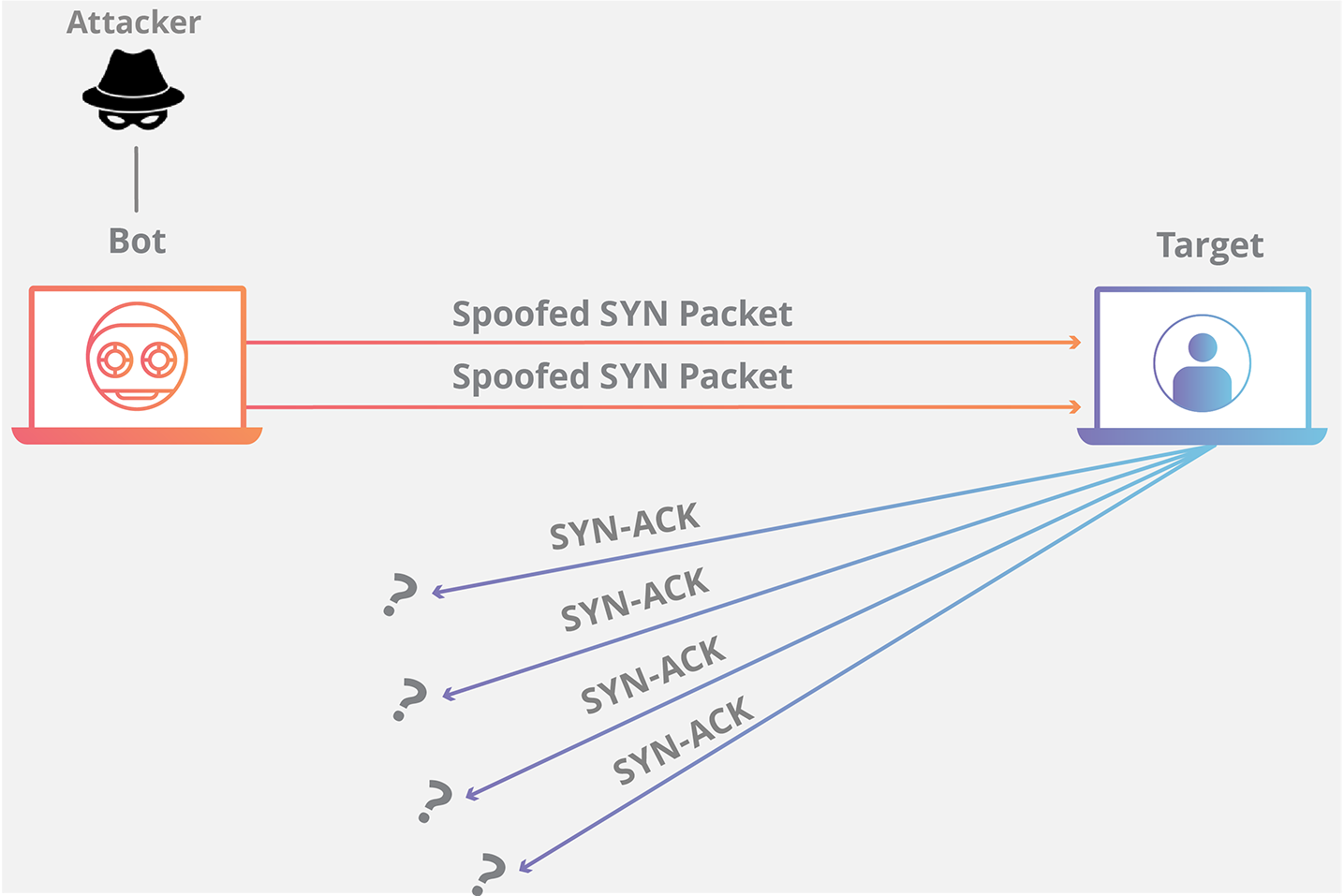
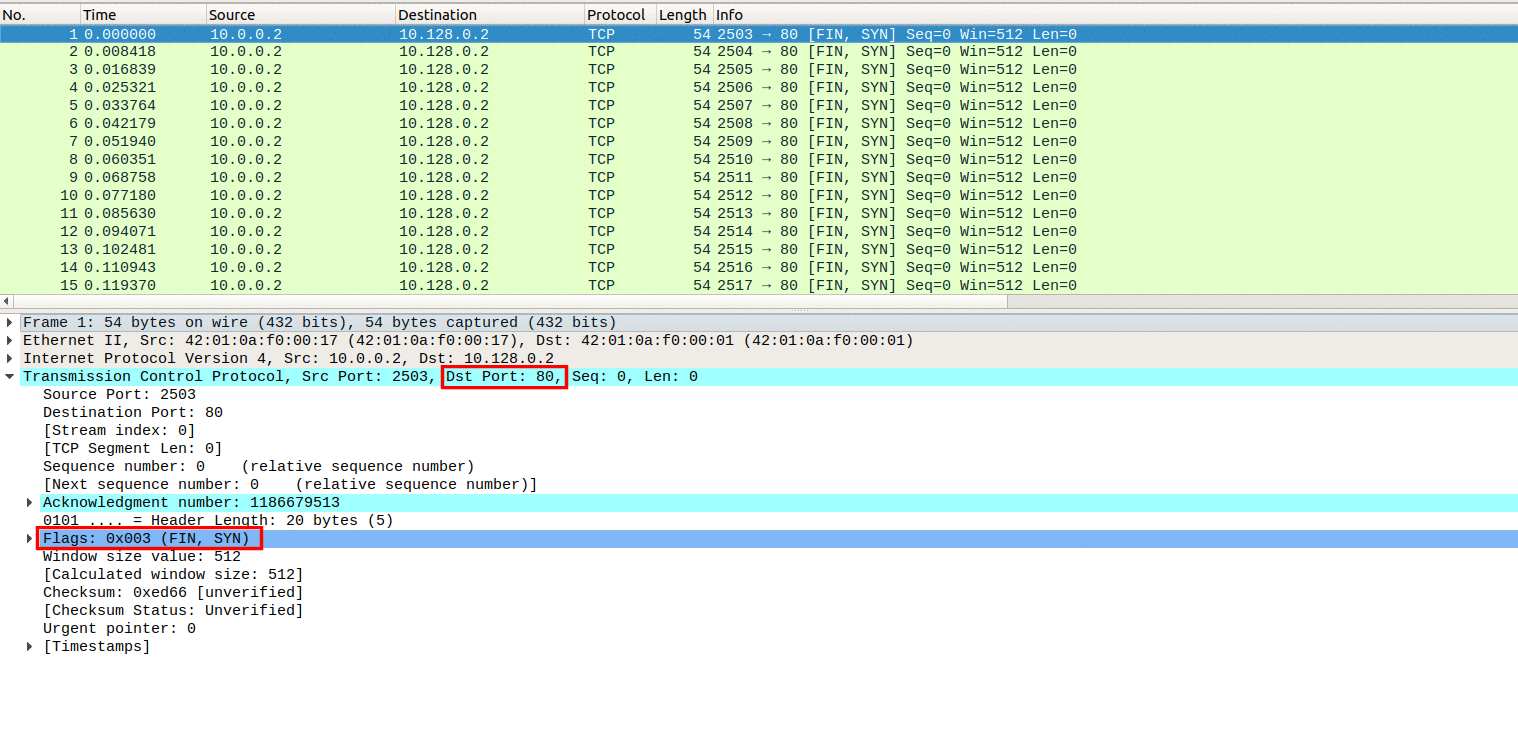
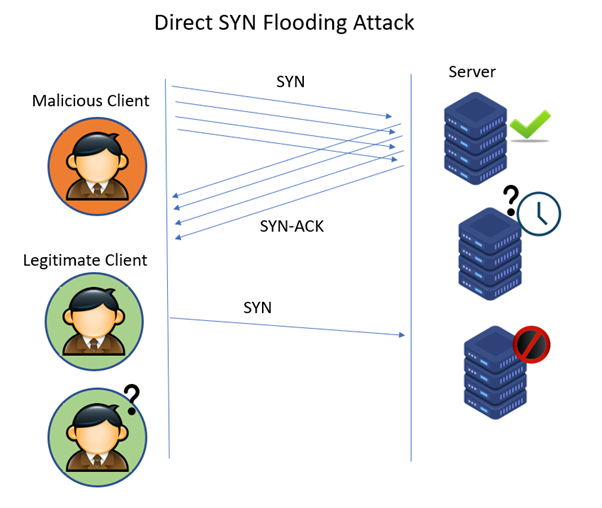
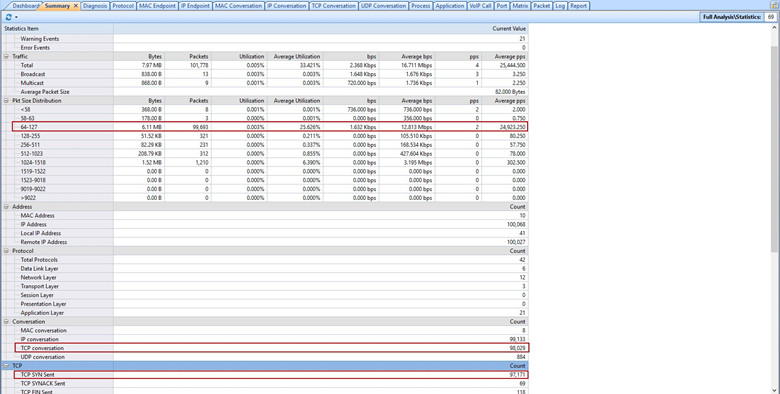
A sure sign of a tcp syn attack. Also, it is preferred to detect an attack early near its source, so that one can easily trace the flooding. To detect syn flooding attacks, which is immune to the syn flooding attacks.
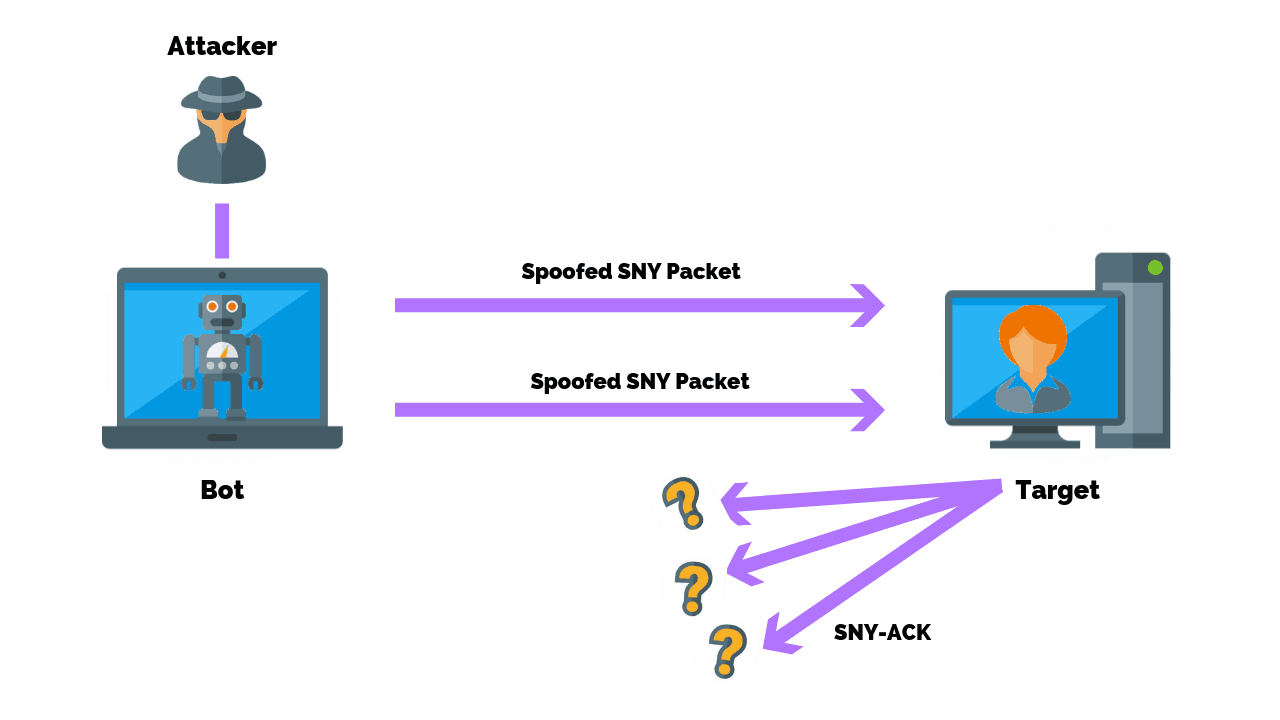
1 a syn flood attack is not visible at the level of normal tcp sockets. The flooding sources must be inside the subnet to. If you have multiple source hosts, you need to track by destination (you will probably want to track by destination either way for this).
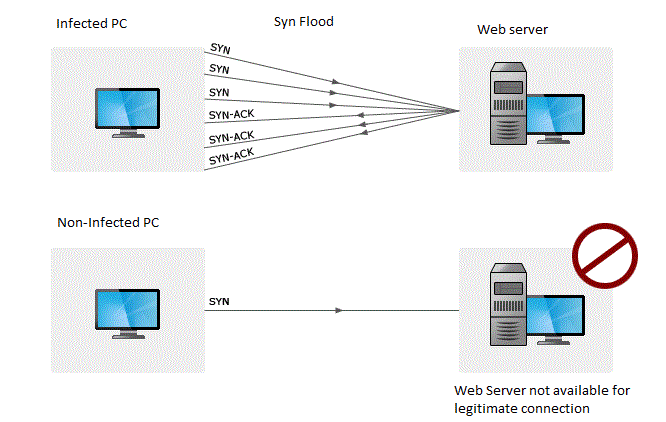
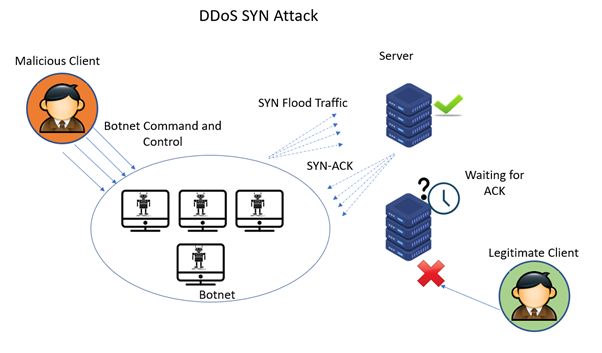
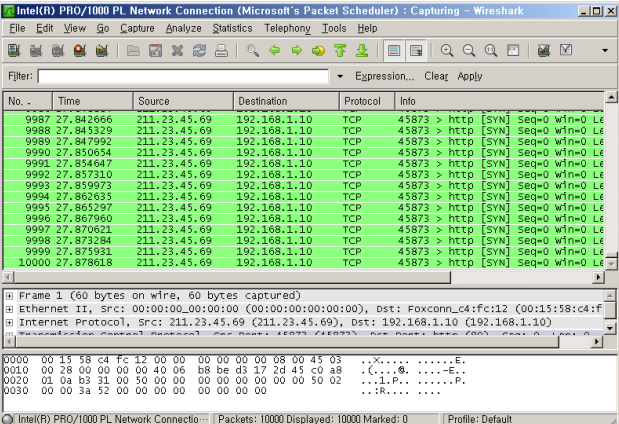
This command will generate tcp syn flood. About press copyright contact us creators advertise developers terms privacy policy & safety how youtube works test new features press copyright contact us creators. Capture the packet on the target host or.
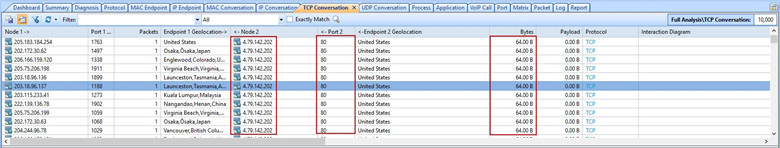
Detecting and investigating unusual network traffic fortunately, there are a number of software that can detect such attacks. Perform tcp syn flood attack against a target server. When we filter with tcp.flags.syn == 1 and tcp.flags.ack == 1 we can see that the number of syn/acks is comparatively very small.
This article explains how to detect a syn flood attack using an advanced protocol analyser like colasoft capsa.